The Vulnerability Landscape So Far in 2025 — What It Means for Security Leaders
CVE volume and exploit speed have surged in 2025. With most teams able to fix only one in ten issues, and attackers moving within hours, vulnerability management has become a scale problem that demands a threat-led and automated approach.

I did a double take recently when running CVE analysis and uncovered this:
27% of all CVEs published since 1999 were released in just the past two years.
If it feels like things weren’t always this hectic, you’re right.
The surge in vulnerability volume is stretching security programs to their limits. Most teams can only fix around one in ten issues, and the gap between disclosure and exploitation is shrinking — sometimes to just hours.
The reality is hard to ignore:
- 135 new CVEs every day — a 40% year-on-year increase
- 35% of intrusions (according to Google Trends) in 2024 started with a vulnerability exploit (double that of phishing)
- Only 1 in 10 vulnerabilities ever gets fixed
- Time to exploit now measured in hours, not days
- A third of breaches result in someone getting fired
- 50% of security leaders want to quit their job within the next year
Vulnerability management is a problem that is growing faster than the resources most teams have to deal with it.
2025 - The Scale Crisis
The rise in new CVEs is fast, steady, and shows no sign of slowing down. Many teams still depend on older ways of ranking vulnerabilities, but these methods do not work well when almost half of all CVEs get a high score that triggers an SLA.
This is where the real problem shows up. When everything looks urgent, teams struggle to tell what matters and what can wait. This leads to long remediation or ticket lists, slow action, and real risk slipping through.
2025 Data Snapshot - Jan 1st- Oct 31st
The panel below shows how CVSS scores stack up against real‑world threat data. It highlights how much noise teams face when using older scoring methods on their own.
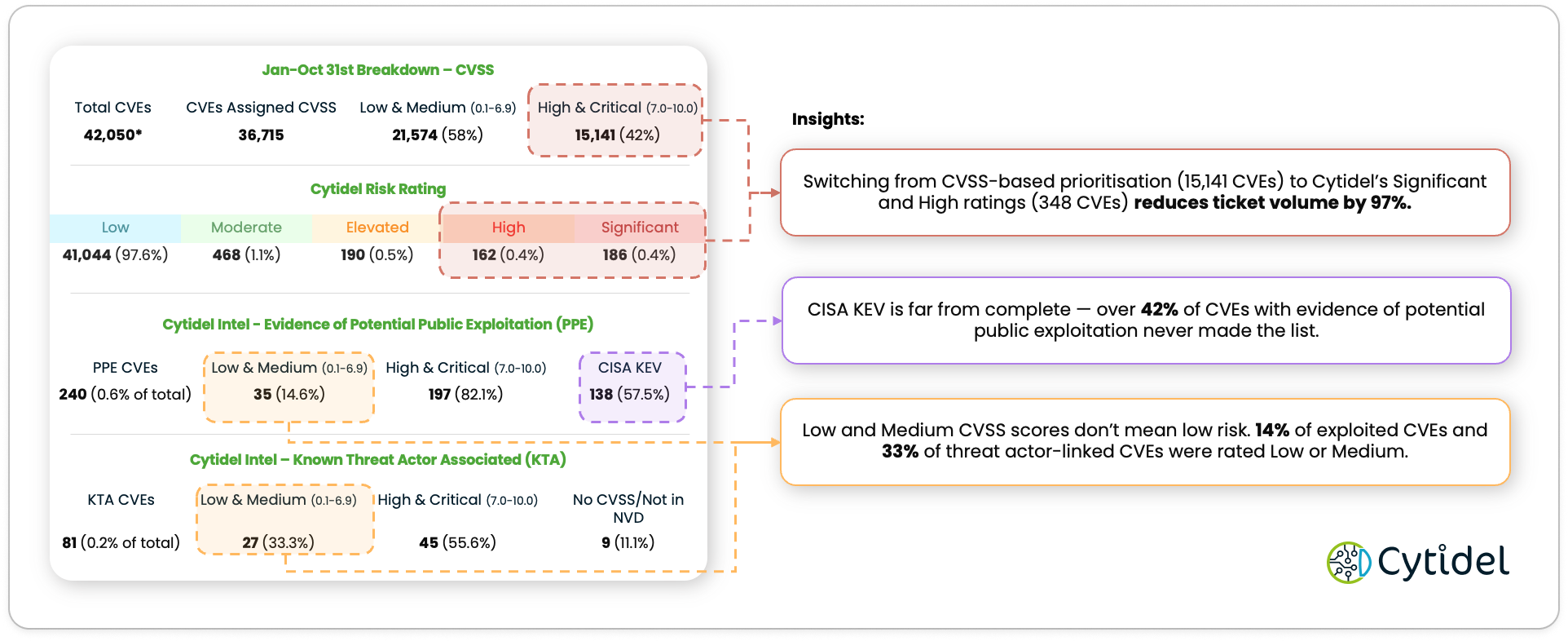
Signal vs Noise
Many teams still depend on CVSS scores or lists like CISA KEV. These help, but they miss key threat activity.
Cytidel data shows:
- 42% of CVEs with signs of public exploitation were not on CISA KEV.
- 14% of exploited CVEs had low or medium CVSS scores.
- 33% of threat actor‑linked CVEs had low or medium scores.
Many of the threats that matter most sit inside groups that look low impact on paper. Teams end up sifting through the endless noise haystack, trying to spot a needle, while the real danger is already moving behind them. When scoring labels downplay active threats, it’s easy to focus on the wrong work and miss what counts.
Its Not Just The Noise - Threats Move Faster Than Process
The speed of attack activity is now the biggest gap for most teams. Exploits can appear within hours of a new CVE, long before scanners or internal review cycles catch up.
No team — even the most mature ones — can keep pace with this by hand.
It is not just the speed that causes strain. It is the amount of information teams are expected to stay on top of: security news, vendor advisories, exploit reports, research posts, social media feeds, proof-of-concept drops, dark-web chatter, bug bounty write-ups, and more.
Each of these sources moves at its own pace, and none of them slow down. By the time teams gather the data they need, the picture has already changed.
The work required to collect, filter, verify, and act on threat signals is now bigger and faster than human workflows can handle.
For large organisations, this strain grows even faster. Every new app, cloud service, business unit, or acquired team brings more assets, more alerts, and more risk signals to sort through.
Expanding the footprint means expanding the noise, but generally with no uplift in an organisations ability to process it.
Third-party risk adds even more pressure. Most organisations depend on a wide mix of vendors and suppliers. A single flaw, or breach, in a partner’s tech can become your problem fast. Tracking these outside risks by hand does not scale, and the workload grows with every new vendor added.
Why Threat‑Led Automation Matters
Scaling vulnerability management doesn’t mean hiring more analysts or throwing more dashboards at the problem.
Our view, is that the automation the mapping of threat intelligence to vulnerabilities is not a “nice to have”, it is the only way to keep pace with the real world.
But first, it means changing how you decide what matters.
A threat-led model flips the process. Instead of asking “what’s critical on paper?”, it asks “what’s active in the wild?", and "what risks are most likely to impact our business?".
By automating the correlation between CVEs, threat actor activity, proof-of-concepts, and exploit chatter, teams can shrink their workload by over 90% — and still improve real-world risk coverage.
That’s the approach Cytidel enables. Providing customers with an advanced threat intelligence capability that delivers continuous, risk-driven analysis on every CVE, pinpointing the critical 1% that matter right now.
Closing Thoughts
The vulnerability problem isn’t new, but the rate of growth is. What’s changing is the pace, the pressure, and the impact.
Security leaders can’t fix scale with more spreadsheets, or even headcount. They need systems that work at scale — systems that focus effort where it counts.
Those that focus on threat‑led methods will be in a far stronger place. The aim is not to fix everything. The aim is to fix the right things first.

![[Updated] Four 9.8s in SolarWinds Web Help Desk: Why We're Flagging This Before Exploitation Hits](/content/images/size/w600/2026/01/solarwinds.png)

