[Updated] Four 9.8s in SolarWinds Web Help Desk: Why We're Flagging This Before Exploitation Hits
![[Updated] Four 9.8s in SolarWinds Web Help Desk: Why We're Flagging This Before Exploitation Hits](/content/images/size/w1200/2026/01/solarwinds.png)
We try not to add to the noise. Most of what we publish focuses on vulnerabilities that are actively being exploited, because that's what actually matters when you're deciding where to spend limited remediation time.
This one is/was different. When we first published this post, there was no confirmed exploitation. We flagged it anyway. As of February 3rd, CISA has confirmed CVE-2025-40551 is being actively exploited in the wild."
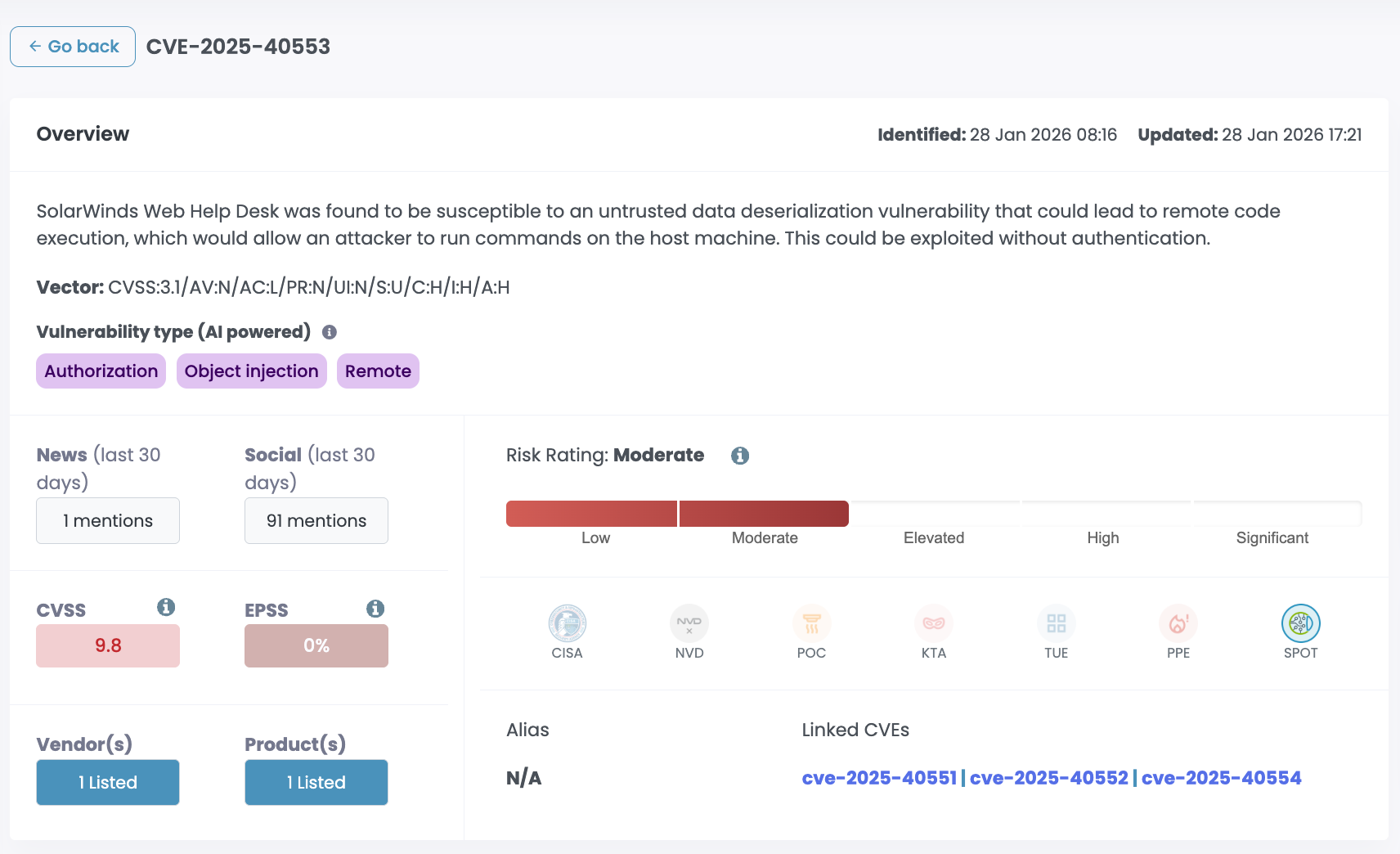
CVE-2025-40551, CVE-2025-40553, CVE-2025-40552, and CVE-2025-40554 are four critical vulnerabilities in SolarWinds Web Help Desk, all scoring 9.8. Two are unauthenticated remote code execution via insecure deserialization. Two are authentication bypass. All four are exploitable over the network with no credentials and no user interaction.
That combination (unauth RCE, network-exposed, trivial to exploit) is catnip for threat actors. We view it likely that reports of exploitation will follow disclosure quickly.
SolarWinds has history
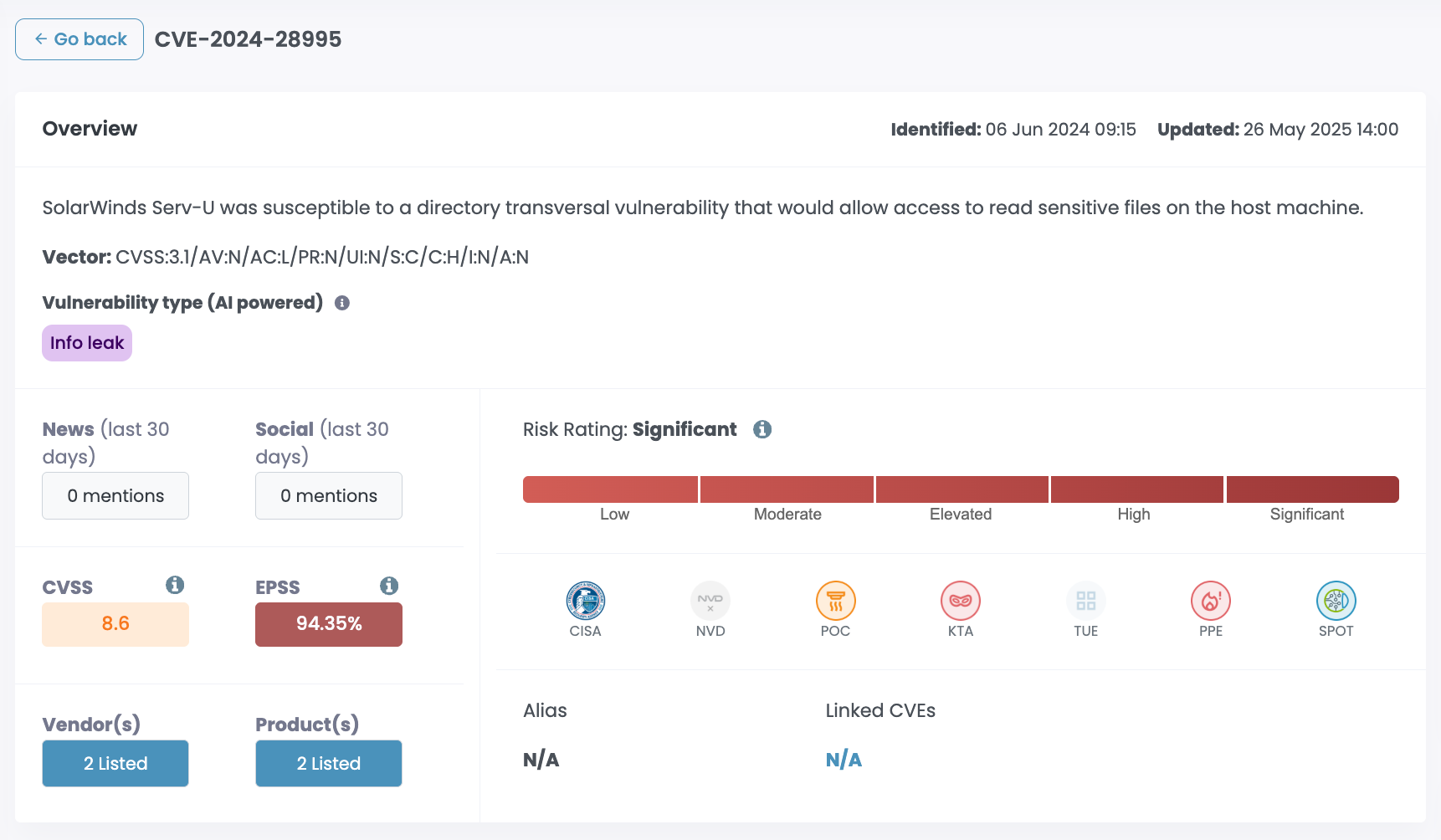
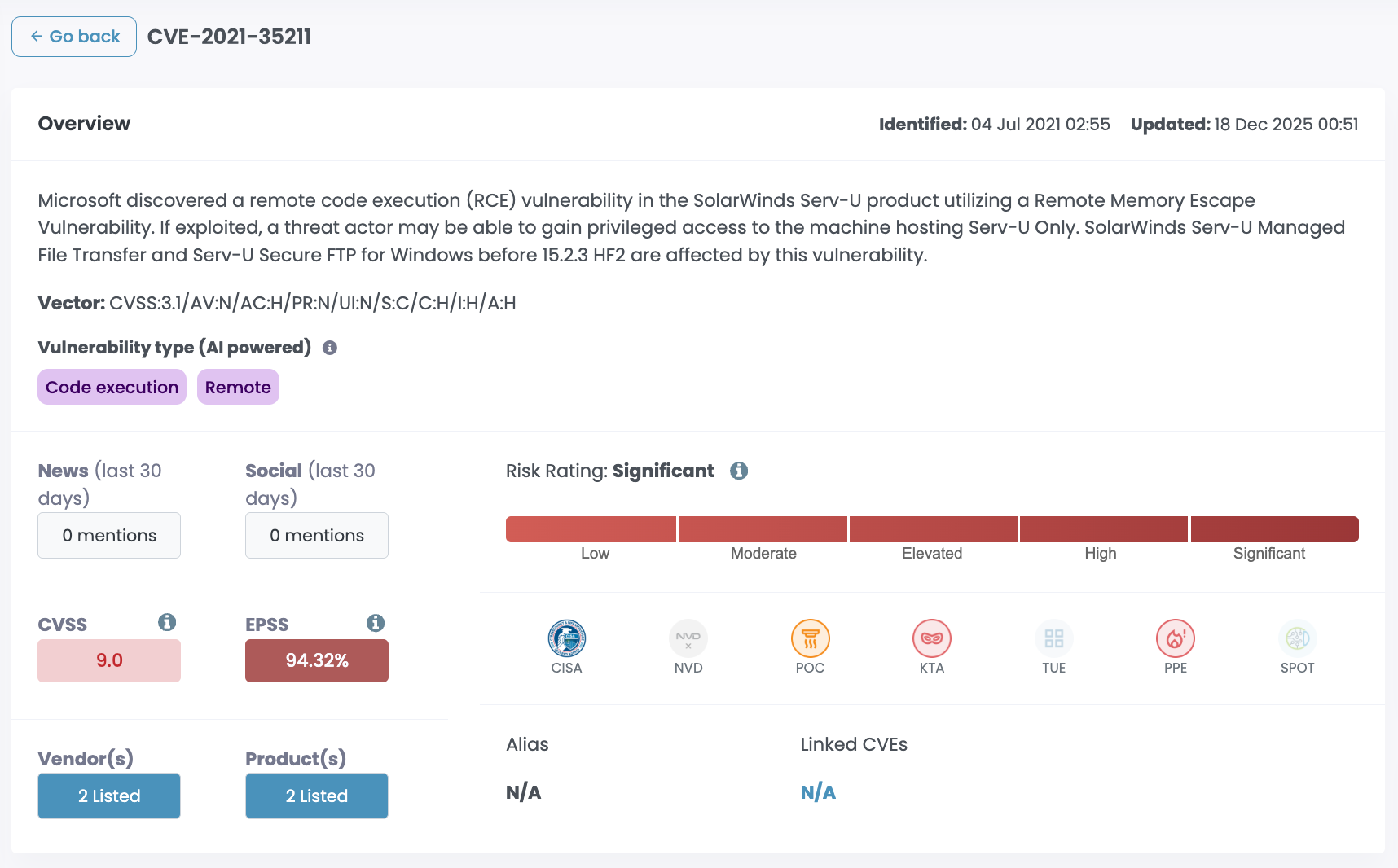
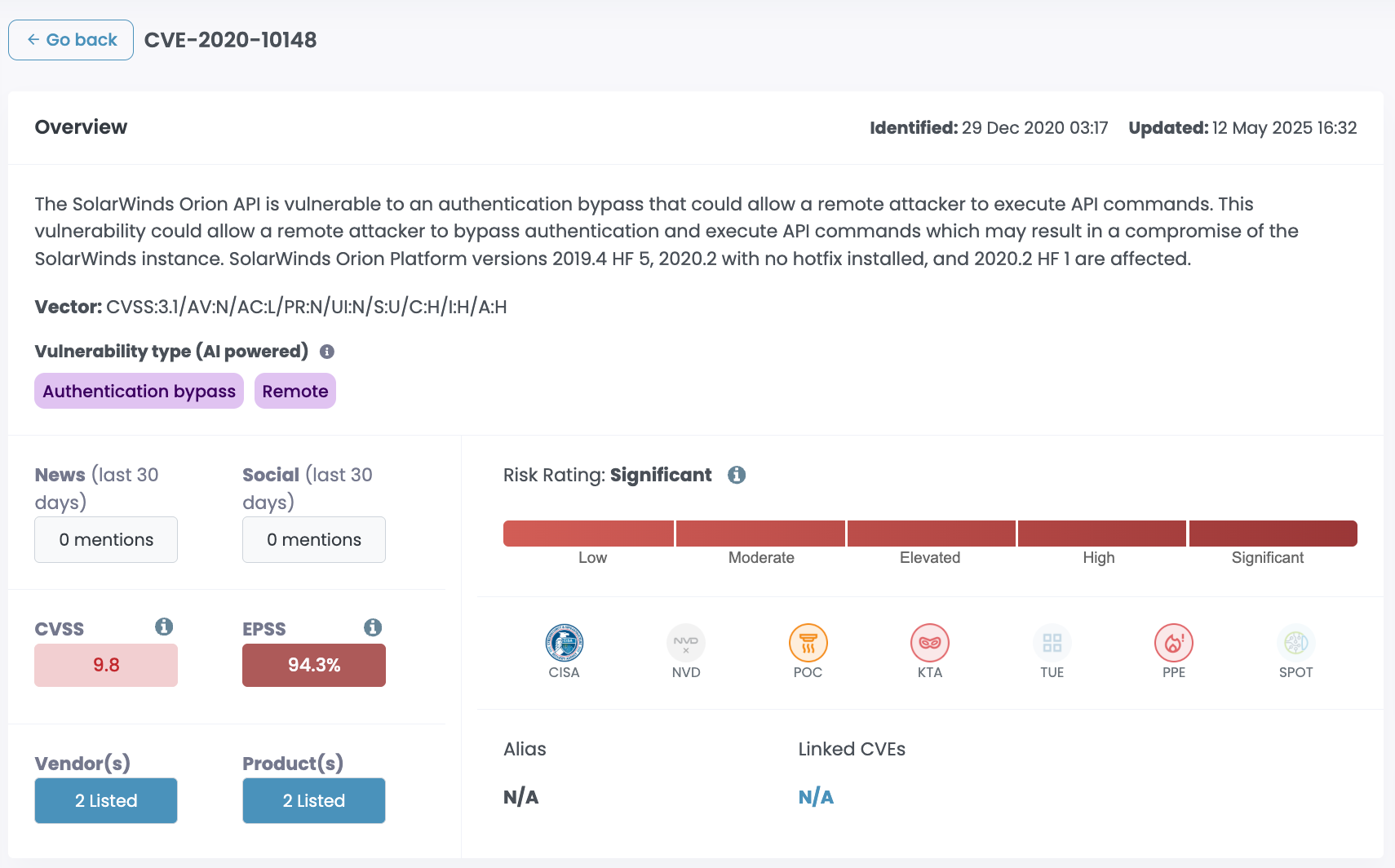
High-profile SolarWinds vulnerabilities in recent years have attracted serious attention. CVE-2024-28995, CVE-2021-35211, and CVE-2020-10148 have all been linked to nation-state actors and sophisticated criminal groups.
High-Profile SolarWinds CVEs
Threat actors known to target SolarWinds products include Lazarus, Kimsuky, Cozy Bear, Fancy Bear, Lucky Mouse, Cl0p, and Cobalt Spider. That's a mix of North Korean, Russian, and Chinese state-sponsored groups alongside some of the more capable ransomware and financial crime operators.
When critical vulnerabilities drop in SolarWinds products, they tend to get weaponised fast. That's part of why we're not waiting for confirmed exploitation on this one.
What's vulnerable
SolarWinds Web Help Desk (WHD) version 12.8.6 and earlier. The fix is version 12.8.9, released January 2026.
The RCE vulnerabilities (CVE-2025-40551 and CVE-2025-40553) sit in the AjaxProxy component. An attacker can send crafted JSON payloads to the AjaxProxy endpoint, triggering deserialization that leads to arbitrary command execution, typically with SYSTEM privileges.
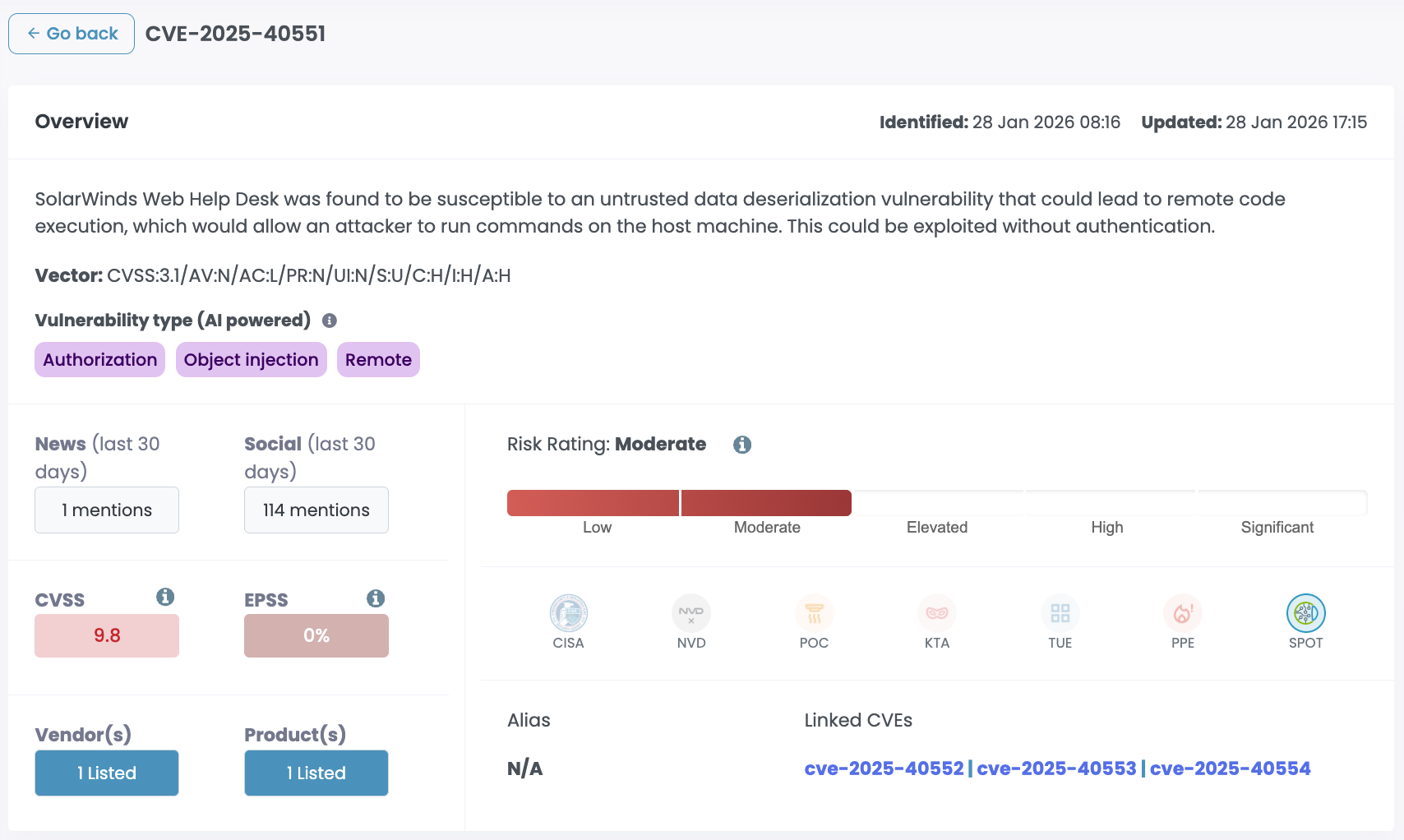
RCE Vulns
The auth bypass vulnerabilities (CVE-2025-40552 and CVE-2025-40554) let attackers skip security checks entirely and access admin functions. Create tickets, delete tickets, extract data, invoke privileged actions. No login required.
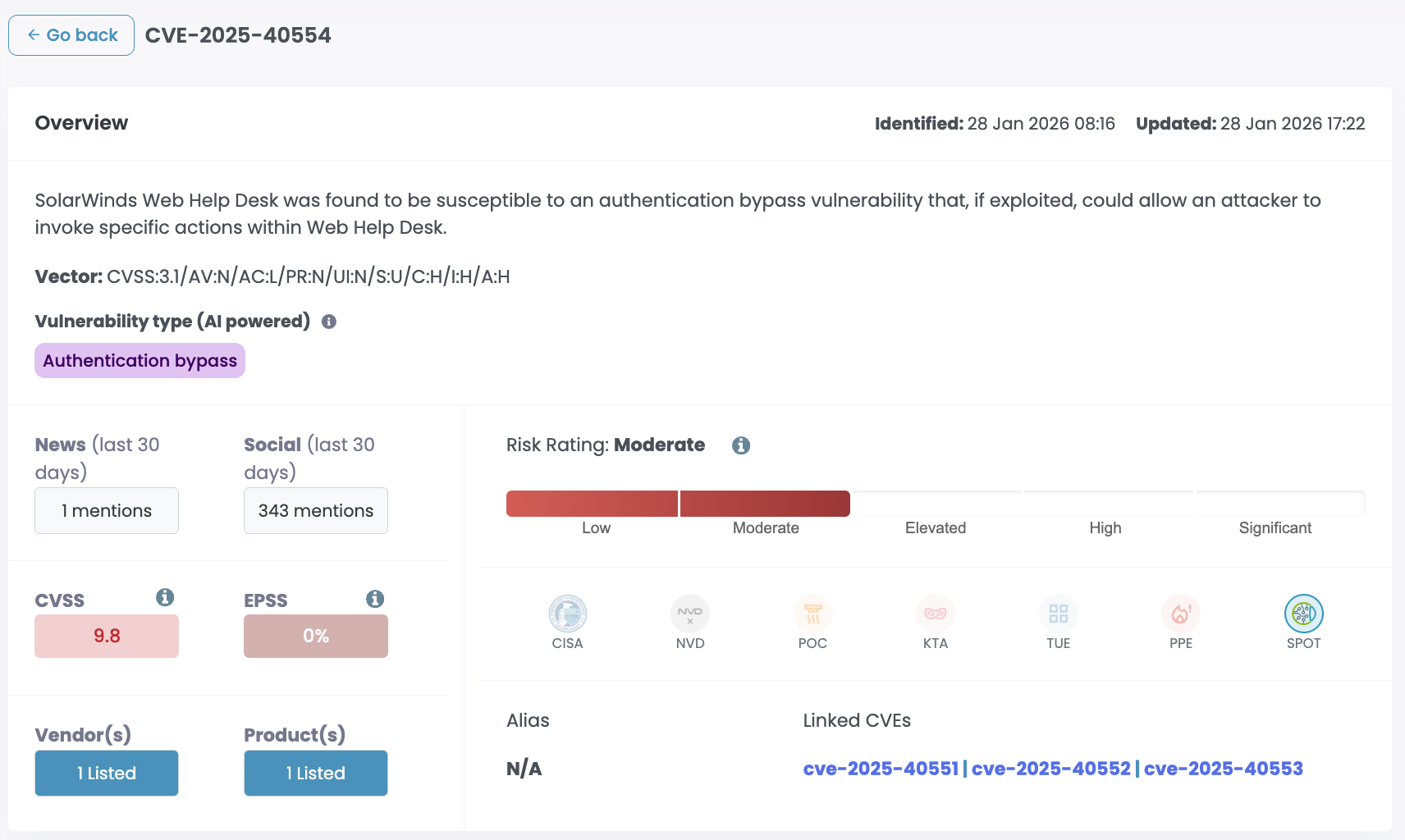
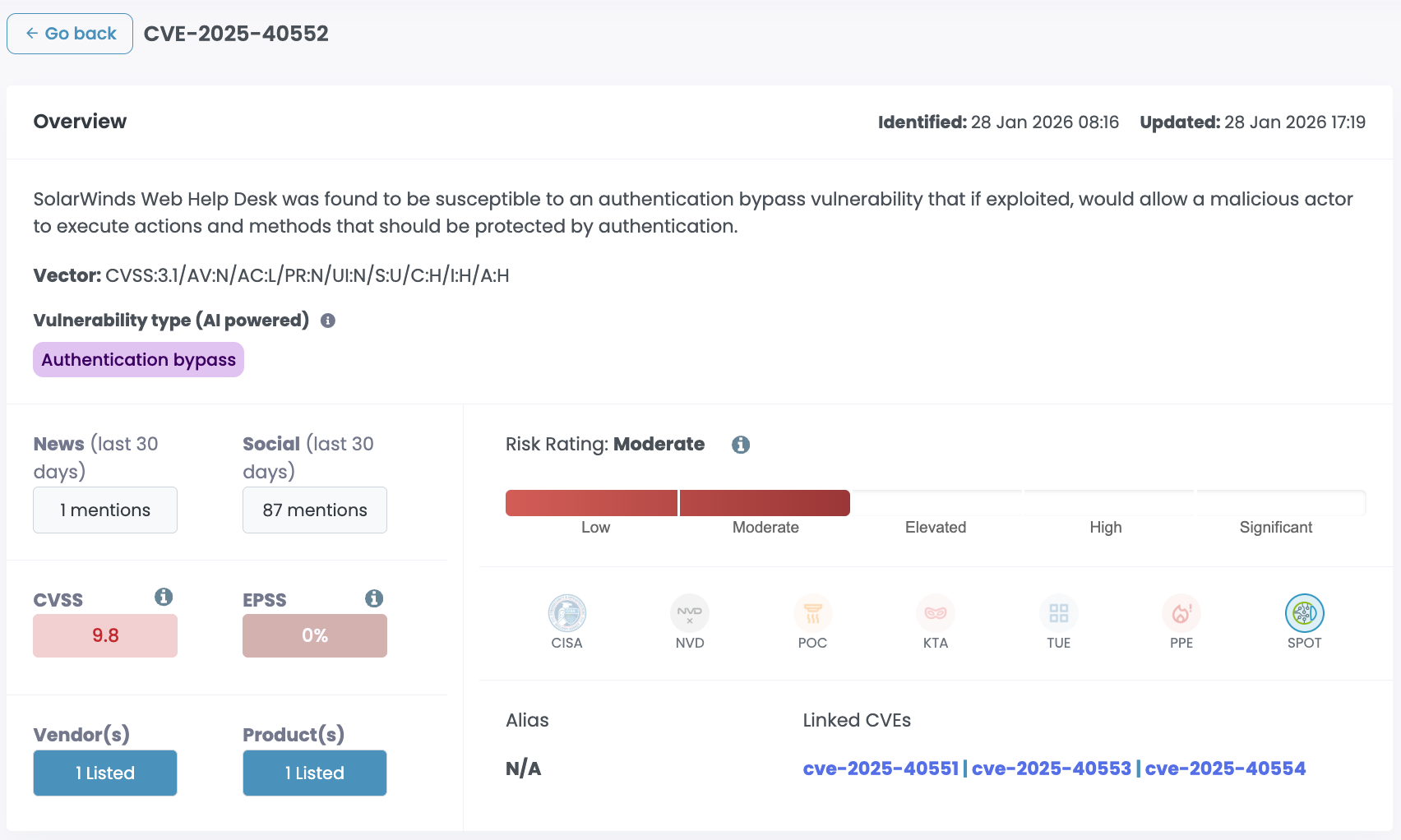
Auth bypass vulns
Why this matters
Web Help Desk is often internet-facing or at least broadly accessible within the network. It handles service tickets, attachments, user records. Stuff that's useful for lateral movement and social engineering.
An attacker who lands unauth RCE on your help desk system has a foothold, SYSTEM-level access, and a trove of internal context about your users and their problems. That's a bad combination.
What to do
Upgrade to 12.8.9. That's the fix for all four CVEs.
If you can't patch immediately:
Restrict network access to WHD servers using firewall rules, ACLs, whatever you've got. Put it behind a VPN or trusted proxy. Deploy WAF rules to filter weird requests to /AjaxProxy. Monitor logs for unauthenticated access or unusual AjaxProxy activity. Consider taking it offline temporarily if it's highly exposed.
After patching, rotate privileged credentials and audit for any unauthorised changes. Check that no legacy instances are lurking behind load balancers.
Exploitation now confirmed
CISA added CVE-2025-40551 to its Known Exploited Vulnerabilities catalog on February 3rd, 2026. Federal agencies have been given three days to patch. CISA hasn't shared details on the specific threat activity, and the ransomware exploitation status is listed as unknown. SolarWinds still hasn't published IOCs, but the fact that it's now in KEV means this is no longer theoretical.
The bottom line
Not every critical CVE deserves the same urgency. But unauth RCE with no user interaction on a commonly internet-facing system, from a vendor with a track record of being targeted by nation-state actors? That's the profile of something that gets weaponised fast.
When we published this on January 28th, exploitation hadn't been confirmed. Six days later, it's in CISA's KEV. If you haven't patched yet, you're now behind the curve
Changelog
- 28 Jan 2026: Original post published
- 3 Feb 2026: Updated to reflect CISA KEV addition and confirmed exploitation of CVE-2025-40551



